Jun 18, 2013 Comments Off on (2010) Internet Traffic from U.S. Government Websites Was Redirected Via Chinese Networks
(2010) Internet Traffic from U.S. Government Websites Was Redirected Via Chinese Networks
Nell’Aprile 2010, il 15% del traffico Internet fu maliziosamente rediretto verso router (e in generale apparati di rete) gestiti da un’operatore di telecomunicazioni Cinese. Parte di questo traffico era destinato a siti di strutture militari e governative Americane. Le operazioni svolte all’interno della rete Cinese non sono ancora ogni documentate e forse non lo saranno mai. La “U.S.-China Economic and Security Review Commission” (http://www.uscc.gov/)ha citato l’evento all’intero del report annuale (2010)
Per continuare la lettura è possibile consultare:
Una descrizione (molto) tecnica dei fatti è disponibile sul blog BGPmon
Nearly 15 percent of the world’s Internet traffic — including data from the Pentagon, the office of Defense Secretary Robert Gates and other U.S. government websites — was briefly redirected through computer networks in China last April, according to a congressional commission report obtained by FoxNews.com.
It was not immediately clear whether the incident was deliberate, but the April 8 redirection could have enabled malicious activities and potentially caused an unintended “diversion of data” from many U.S. government, military and commercial websites, the U.S.-China Economic and Security Review Commission states in a 316-page report to Congress.

China hijack
A draft copy of the report was obtained on Tuesday by FoxNews.com. The final 2010 annual report to Congress will be released during a press conference in Washington on Wednesday.
According to the draft report, a state-owned Chinese telecommunications firm, China Telecom, “hijacked” massive volumes of Internet traffic during the 18-minute incident. It affected traffic to and from .gov and .mil websites in the United States, as well as websites for the Senate, all four military services, the office of the Secretary of Defense, the National Oceanic and Atmospheric Administration and “many others,” including websites for firms like Dell, Yahoo, IBM and Microsoft.
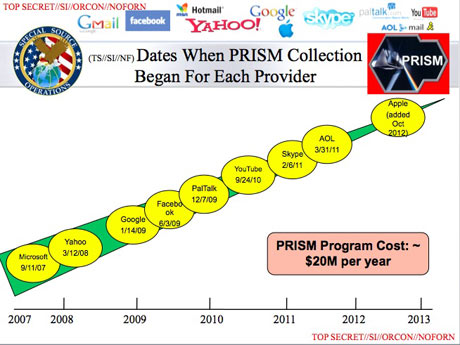 The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post.
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post.